Check Point Research (CPR) sent us an email this morning, saying they’ve spotted an increase in malicious activity in the run-up to Amazon Prime Day 2021, one of the largest online shopping events of the year. This year’s event, slated to occur on June 21-22, promises millions of deals and special offers to Amazon’s 150-million-plus Prime subscribers around the world.
CPR says of particular concern is that nearly 80% of domains containing the word “Amazon” are potentially dangerous. CPR also reports that cybercriminals are impersonating the Amazon brand ahead of the annual shopping event in order to trick people into credential theft of their email addresses, payment details and passwords, and more:
- In the last 30 days, over 2300 new domains were registered about Amazon, a 10% increase from the previous Amazon Prime Day, where the majority now are either malicious or suspicious
- Almost 1 out of 2 (46%) of new domains registered with the word “Amazon” are malicious
- Almost 1 out of 3 (32%) of new domains registered with the word “Amazon” are deemed suspicious
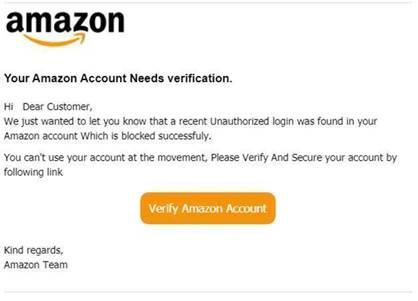
Why Cybercriminals Spoof Domains
Domain spoofing is a popular way for cybercriminals to steal money or sensitive data. Look-alike domain registrations aim to divert online traffic and redirect unsuspecting consumers to websites that contain malware, or prompt users to provide personal identifying information. In this case, cybercriminals are aiming to hide behind the Amazon brand, so that they can target Prime Day shoppers with emails that prompt the recipient to click a malicious link or respond with sensitive information.
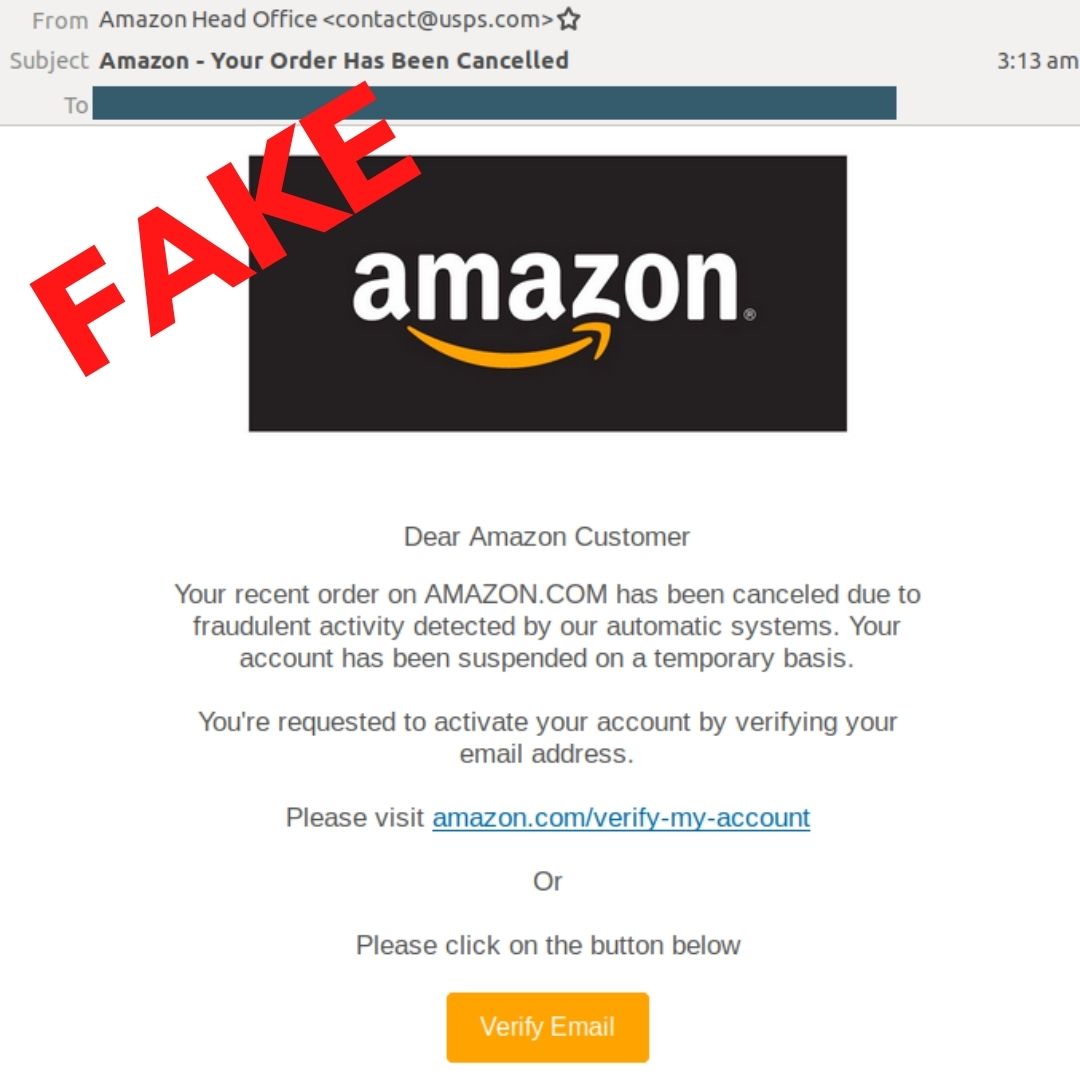
Example A: Impersonation of Amazon’s “Customer Service”
Here’s an example CPR found of a phishing mail, allegedly sent from Amazon’s “Customer Service.” The email prompts the opener to verify their Amazon account. CPR determined that the email was never sent by Amazon, but instead is clear phishing from (admin@fuseiseikyu-hl[.]jp). The attacker here tries to lure victims into clicking on a malicious link, which redirects the user to http://www[.]betoncire[.]es/updating/32080592480922000. The link is now inactive.
Example B: Fake Website Imitating Amazon Japan
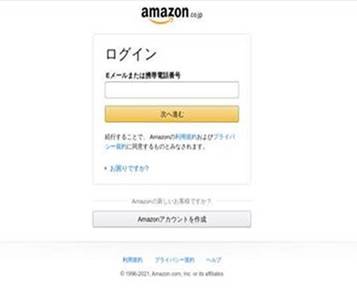
Another example that CPR found is an imitation of Amazon Japan. CPR determined that the page, with the URL: amazon[.]update-prime[.]pop2[.]live, is indeed malicious.
Ekram Ahmed, a Spokesperson at Check Point Software wrote in an email,
“Prime Day is a prime opportunity for cybercriminals. The danger here is being tricked into giving up your credit card info, your passwords, and even your home or email address to cybercriminals. Their goal is to make money off your personal details. The tactic cybercriminals use for their deception is domain spoofing, where you click on a page that appears to be from Amazon, but you’re actually on malicious ground. Clearly, cybercriminals are doubling down on Prime Day this year, as almost all the domains around “Amazon” have red flags.”
Check Point’s suggestions for staying safe Prime Day:
1. Watch for misspellings of Amazon.com. Beware of misspellings or sites using a different top-level domain other than Amazon.com. For example, a .co instead of .com. Deals on these copy-cat sites may look just as attractive as on the real site, but this is how hackers fool consumers into giving up their data.
2. Look for the lock. Avoid buying something online using your payment details from a website that does not have secure sockets layer (SSL) encryption installed. To know if the site has SSL, look for the “S” in HTTPS, instead of HTTP. An icon of a locked padlock will appear, typically to the left of the URL in the address bar or the status bar down below. No lock is a major red flag.
3. Share the bare minimum. No online shopping retailer needs your birthday or social security number to do business. The more hackers know, the more they can hijack your identity. Always maintain the discipline of sharing the bare minimum when it comes to your personal information.
4. Always note the language in the email. Social engineering techniques are designed to take advantage of human nature. This includes the fact that people are more likely to make mistakes when they’re in a hurry and are inclined to follow the orders of people in positions of authority. Phishing attacks commonly use these techniques to convince their targets to ignore their potential suspicions about an email and click on a link or open an attachment.
5. Before Prime Day, create a strong password for Amazon.com. Once a hacker is inside your account, it is game over. Make sure your password for Amazon.com is uncrack-able, well before June 21st.
6. Don’t go public. If you find yourself at an airport, a hotel or your local coffee shop, please refrain from using their public wi-fi to shop on Amazon Prime Day. Hackers can intercept what you are looking at on the web. This can include emails, payment details, browsing history or passwords.
7. Beware of “too good to be true” bargains. This will be tough to do, as Prime Day is all about great offers. But, if it seems WAY too good to be true, it probably is. Go with your gut: an 80% discount on the new iPad is usually not a reliable or trustworthy purchase opportunity.
8. Stick to credit cards. During Prime Day, it’s best to stick to your credit card. Because debit cards are linked to our bank accounts, we’re at much higher risk if someone is able to hack our information. If a card number gets stolen, credit cards offer more protection and less liability.
Be sure to reach out to us on Facebook, Twitter, or Instagram if you have questions, comments, or just want to say “hi.”
